Annexures
Table of contents
Overview
This page contains the various annexures referenced throughout the Fraud Risk Assessment Leading Practice Guide.
Related tools annexures
Annex A is an overview of the different fraudster personas. These can be viewed on the Discover different types of fraudsters page.
This business process map for a hypothetical government services program illustrates how to use Fraudster Personas to identify points at which someone might commit fraud against the program.
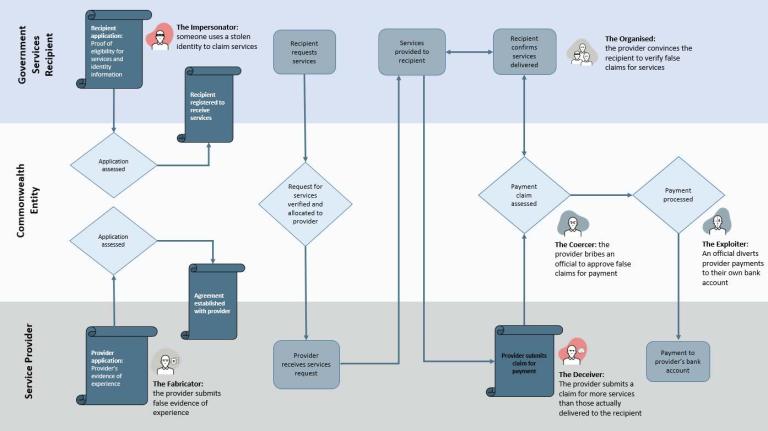
This Diagram illustrates where fraud risks in provision of government services might be illustrated by using fraudster personas.
- Recipient registration Step 1: Recipients of government services submit applications to register to receive services, which are then assessed by government entities. If successful, a recipient is registered to receive services. (This part of the process could be targeted by an impersonator using a stolen identity to claim services.)
- Third-party provider registration Step 1: Third-party providers of government services submit applications to provide a service, which government entities then assess. If successful, providers enter into agreements with government entities on service provision. (This part of the process could be targeted by a fabricator submitting false evidence of experience to improve their application.)
- Claim for services Step 1: A recipient requests services, and once the request is verified, the request is passed on to a provider that provides services to the recipient.
- Claim for services Step 2: The service provider submits a claim for payment to the government. (This part of the process could be targeted by a deceiver submitting a claim for more services than were actually delivered to the recipient.)
- Claim for services Step 3: The recipient confirms the delivery of services. (This part of the process could be targeted by organised fraudsters convincing the recipient to verify false claims.)
- Claim for services Step 4: The payment claims are assessed. (This part of the process could be targeted by a coercer bribing officials to approve false claims for payment.)
- Claim for services Step 5: The payment is then processed. (This part of the process could be targeted by an exploiter diverting provider payments to their own bank account.)
- Claim for services Step 6: Finally, the payment is delivered to the provider for services delivered.
End of alternative text
When conducting interviews with senior executives the interviews should be structured around a set agenda and could consider the following questions relating to their Group/Division/Branch/Program:
- What is your opinion on opportunities for fraud in your area of responsibility?
- What are the delegations of authority and financial accountabilities in your area of responsibility?
- What monitoring and oversight mechanisms are in place?
- What are the roles and responsibilities of key personnel?
- Can you provide a high-level description of the key financial processes and systems in place?
- What are the monitoring and oversighting mechanisms?
- What is your opinion on internal pressures in your area of responsibility?
- Can you comment on the performance of individual business units?
- Are there any cultural issues or challenges (such as attitude towards mistakes), or morale issues?
- Has there been any recent changes in structure, function or systems?
- Do any of your business have high levels of staff turnover?
- Have there been any previous incidents, including suspected and actual fraud/s?
- Are you able to share the results of recent internal or external audits, or third party assurance reviews?
- Do staff in your area of responsibility have a good awareness of entity fraud control arrangements, including mechanisms for reporting suspected fraud and misconduct?
- Are there any concerns you have or any other relevant issues you wish to raise?
Risk identification
- Risk number (for tracking)
- Fraud risk description (actor, action, outcome / impact)
- Fraud risk owner and key business contact
- Applicable Fraudster Persona (to help with reporting)
Risk analysis – recording current controls
- A short active title/description of each existing control (e.g. ‘system controls only allow limited authorised users to change bank accounts’)
- The following control attributes:
- Control number (for tracking)
- the type of control (prevention, detection, response)
- a description of what the control does to mitigate the risk
- an assessment and rating of control effectiveness
- the owner of the control
- an indication if further monitoring or assurance is required
- An overall assessment of the control environment including control gaps or enablers (e.g. missing controls, barriers to data sharing, prevalence of false identities or perverse incentives)
- A description of the residual risk once fraud controls are taken into account
- Likelihood rating (this can include the probability that the fraud risk will happen and/or the frequency the business may expect the fraud risk to occur)
- Consequence rating (this can include the possible duration of fraud and the impact it could cause)
- Current risk rating (this can include the rationale and/or evidence used for this rating)
Risk evaluation
- If a decision is to maintain existing controls and monitor a risk, record what this means and a future review date
- If a decision is to change or discontinue an activity to eliminate a risk, record reasons why (e.g. the costs to mitigate the risk were too high)
- If a decision is to retain a high-level risk and not apply treatments, record reasons why (e.g. the anticipated benefits of the activity outweigh the consequences of the risk, or the costs of additional treatment, or the timeframes to implement additional treatments, would have a negative impact on the outcomes of the activity)
- If a decision is to undertake further risk analysis, such as conducting an audit or ‘pressure test’ of the existing controls, record the action to be taken and when this will be completed
- If a decision is to transfer a risk, record the new owner and when it will be transferred
Risk treatment
- If a decision is to treat a risk, record:
- The current risk rating and the target risk rating
- Treatment number (for tracking)
- A short active description of the proposed treatment or control
- The type of control (prevention, detection, response)
- A description of what the control will do to mitigate the risk
- A description of the implementation process
- The treatment owner
- The implementation timeframe
The Commonwealth Fraud Prevention Centre has developed a Fraud Risk Assessment Template that includes fields for all of these data points fraud risks. To obtain a copy please contact the Centre at info@counterfraud.gov.au.
Risk Analysis Matrix (example only)
|
Likelihood |
Consequences |
||||
|
Insignificant |
Minor |
Moderate |
Major |
Severe |
|
|
Almost certain |
Low |
Medium |
High |
Very high |
Very high |
|
Likely |
Low |
Medium |
Medium |
High |
Very high |
|
Possible |
Low |
Low |
Medium |
High |
High |
|
Unlikely |
Very low |
Low |
Low |
Medium |
High |
|
Rare |
Very low |
Very low |
Low |
Medium |
Medium |
Risk Management Action Table (example only)
|
Risk rating |
Level of action required |
|
Very high |
The risk is beyond the entity’s risk tolerance and appetite and must be immediately mitigated or avoided. Regular review and reporting of the risk needs to be provided to Senior Executive and all relevant stakeholders. |
|
High |
The risk should be mitigated or avoided, unless the anticipated benefits of the activity outweigh the consequences of the risk. Regular review and reporting of the risk needs to be provided to relevant stakeholders, and senior executive at their discretion. |
|
Medium |
The risk may be acceptable and regular review and reporting of the risk needs to be provided within the relevant business unit and to affected stakeholders. |
|
Low |
The risk is generally acceptable but must be monitored to make sure that the risk rating does not change. |
|
Very low |
The risk is acceptable. |
Controls are individual measures, processes or functions that help entities prevent, detect and respond to fraud. An integrated assembly of controls make up a control environment. There are three high level categories of controls:
Prevention
Prevention controls are the most common and cost-effective way to mitigate fraud. They reduce the likelihood and consequences of fraud by preventing or limiting the extent of the risk occurring.
Prevention controls can include people or process controls to increase transparency and influence behaviours, or processes and technology-based controls to stop or limit fraudulent activity.
Detection
Detection controls can help to identify when fraud has occurred. They can help disrupt additional fraud and mitigate the consequences. Detection controls are not as cost effective as prevention controls. However, if detected early, the impacts of fraud can be significantly reduced.
Detection controls can include people and process controls such as fraud aware staff and tip-off processes, or technology-based controls such as fraud detection programs.
Response
Response controls respond to fraud after it has occurred. They help to reduce the consequences or disrupt additional consequences. Response controls are not as cost effective as prevention or detection controls. However, if implemented effectively, the present and future impacts of fraud can be significantly reduced.
Response controls can include people and process controls such as trained fraud investigators and investigation processes, or technology-based controls such as audit logging and surveillance.
Further information about specific strategies and fraud controls is available at CounterFraud.gov.au.
When assessing the effectiveness of the controls, it can be useful to anticipate the behaviour of a fraudster (such as provided in Annex A). Applying a sceptical mindset helps you consider whether a fraudster could override or find a way around a control. Trying to answer the following questions can help in assessing the effectiveness of controls:
- What is the objective of the control and its unique role in managing the risk?
- What assumptions were made about the purpose and effectiveness of the control?
- Does the control work as designed? How do you know?
- Is the control relevant and up-to-date?
- Is the control automated or applied by people? If applied by people, how do you know they are applying the control consistently or correctly?
- What are the activities that support or enable the control?
- Are there backup controls or fail-safes that would apply if the control did not work?
- Does the control lead to any unintended changes in behaviour?
The Commonwealth Fraud Prevention Centre has developed a Commonwealth Pressure Testing Framework to guide entities on testing of the effectiveness of fraud controls after they have been implemented through the fraud risk assessment process.
The following Control Assessment Rating Table can also help with rating the effectiveness of controls. It uses qualitative and quantitative considerations when determining a control’s effectiveness. The traffic light system is a useful way to communicate where controls are effective or where vulnerabilities require action.
| Rating | Quantitative considerations | Qualitative considerations | Action required |
| Effective |
|
|
|
| Partially effective |
|
|
|
| Ineffective |
|
|
|
The ‘SMART’ principle (Specific, Measurable, Achievable, Relevant, Timed) can be applied to help co-design controls with key risk stakeholders.
Specific
The control should have a clear and concise objective. They should also be well defined and clear to anyone with a basic knowledge of the work. Consider: who, what, where, when and why.
Measurable
The control and its progress should be measurable. Consider:
- What does the completed control look like?
- What are the benefits of the control and when they will be achieved?
- The cost of the control (both financial and staffing resources).
Achievable
The control should be practical, reasonable and credible and they should also consider the available resources. Consider:
- Is the control achievable with available resources?
- Does the control comply with policy and legislation?
Relevant
The control should be relevant to the risk. Consider:
- Does the control modify the level of risk (through impacting the causes and consequences)?
- Is the control compatible with the entity’s objectives and priorities?
Timed
The control should specify timeframes for completion and when benefits are expected to be achieved.

